The EU's Cyber Resilience Act: Prepare your business
By Gil KATZ on September 10, 2025

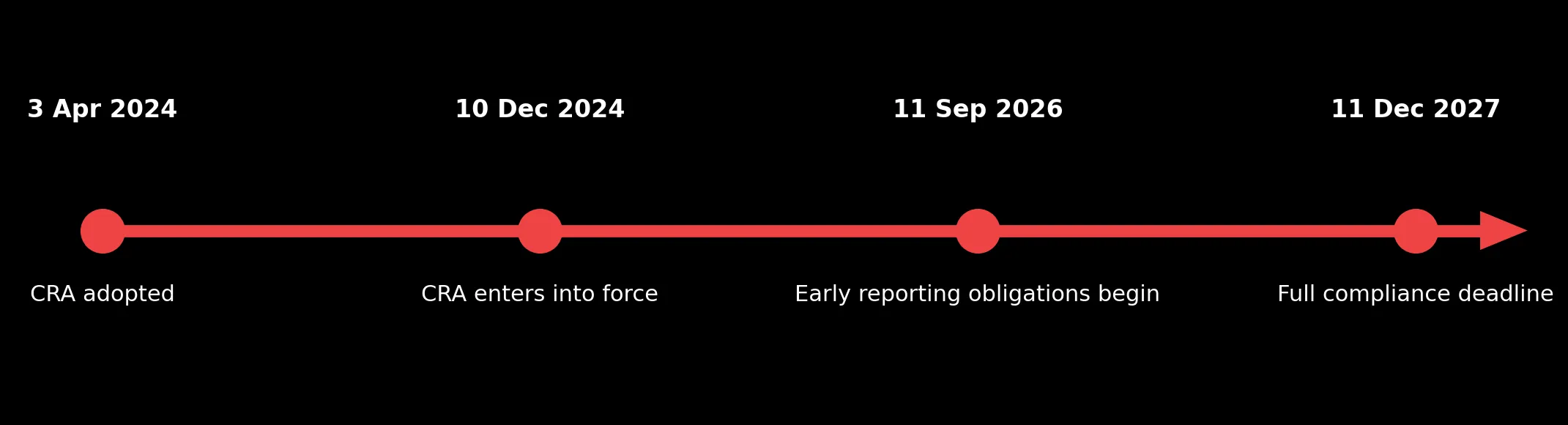
Officially entering into force in November 2024, the EU’s Cyber Resilience Act (CRA) gave business three years in total to prepare before requiring full compliance with the new regulation. As we approach obligations gradually coming into effect, now is a great time to start to prepare!
Some readers may remember vividly, as I do, the entering into effect of GDPR regulation, which was accompanied by significant uncertainty. While the EU commission clearly learned some lessons from that process and made efforts to assure that the application of the CRA would be as consistent as possible across the continent, some ambiguity is still present in the legislation. Moreover, translating complicated legal-speak to a concrete action plan for your company’s specific case is a challenging process. In this article we’ll try to make this process as clear as possible.
What is the Cyber Resilience Act?
The Cyber Resilience Act is a new regulation, passed by the EU’s institutions in 2024. While the law is already in the books, application of the different obligations it specifies will start in one year, with full application of all obligations in December of 2027. This transition period gives companies the time to prepare. While each company’s situation is different, some teams may face significant refactoring to complete before that date.
The CRA represents a major shift in how digital products are conceived and brought to market. It establishes cybersecurity as a design requirement, meaning that security must be built into products and services from the start, not as an afterthought. This approach aims to reduce vulnerabilities at their source, rather than relying solely on patching or reactive measures.
This isn’t just about ticking a compliance box. It’s about making Europe’s digital infrastructure tougher and more trust-worthy. When every connected product, from cloud platforms to industrial software, meets the same high security standards, the whole ecosystem becomes harder to attack. For customers, it means greater confidence that the tools they rely on are built to protect them from the start. For businesses, that means more resilient operations, but also potentially higher development costs, especially for those businesses that would be unable to adapt and comply with the new regulation efficiently.
For companies already working under frameworks such as DORA or NIS2, the CRA provides another layer of assurance, aimed directly at the security of their digital supply chain. By setting EU-wide rules for the cybersecurity of products with digital elements, it helps to ensure the tools and services businesses in sensitive industries depend on are as resilient as their internal processes ought to be.
Is my business concerned by the CRA?
Relative to existing regulation such as DORA or NIS2, the CRA extends to many more business categories. Article 2 states that “this regulation applies to products with digital elements made available on the market, the intended purpose or reasonably foreseen use of which includes a direct or indirect logical or physical data connection to a device or network”. This is a very broad definition, which makes it almost impossible to imagine any digital service that falls outside this scope. While open-source projects are exempt, as long as they are not for-profit, businesses would have to adjust. Failing to do so may result in significant fines of up to $15M or 2.5% of the business’ worldwide turnover.
The text specifically states that it applies to all economic operators including manufacturers, importers, distributors and authorized representatives (article 3). Moreover, “products with digital elements” include standalone software, meaning SaaS providers and software developers are caught under the “manufacturer” definition. This broad scope means that even companies that don’t consider themselves as tech companies may still be covered. For example, a manufacturer of industrial equipment that includes connected sensors, or a retail chain that provides its customers with cloud-connected point-of-sale systems or loyalty apps, would still be covered by the CRA. Similarly, companies that import or distribute connected devices or software into the EU market are also covered, even if they played no role in the original design.
Another important implication is the shared responsibility across the supply chain. Under the CRA, security is not just the manufacturer’s problem. Importers, distributors, and authorized representatives have their own obligations to ensure that the products they handle comply with the regulation. This means businesses will need to pay closer attention to the security posture of their suppliers and partners, and in many cases, request formal assurances or documentation of CRA compliance before engaging with them. For many organizations, this will require new procurement procedures, risk assessments, and ongoing monitoring.
Still not sure if the CRA applies to you? If you check any of these boxes,it probably does. The CRA applies to your business if it:
- Designs or develops software or hardware with any internet or network connection
- Provides SaaS or other cloud-based services to EU customers
- Imports connected products or software into the EU market
- Distributes connected devices or software within the EU
- Acts as an authorized representative for a non-EU manufacturer
- Embeds or integrates third-party digital components into your own products
If you tick any of these boxes, you will need to ensure the products you make available in the EU comply with the CRA’s requirements, even if your core business is not traditionally “technology.”
Requirements of the CRA
The CRA sets out a series of obligations aimed at making connected products more secure throughout their entire lifecycle. These requirements apply not just when a product is launched, but also for years afterwards, ensuring that security is actively maintained. While details vary depending on your role in the supply chain, most obligations fall into a few clear categories:
- Incident reporting: If you discover that your product is being actively exploited, you must report it to the ENISA (EU Agency for Cybersecurity) and to the CSIRT (Computer Security Incident Response Team) within 24 hours. This tight timeline is designed to speed up the sharing of critical threat information and reduce the time attackers can operate undetected.
- Vulnerability management & governance: Businesses must have a process in place to identify, assess, and fix vulnerabilities, both before release and throughout the product’s support period. This includes proactive security testing, risk assessment, and maintaining secure configurations by default.
- Secure design & documentation: Security can no longer be an afterthought. Products must be developed with security built in from the start, with clear technical documentation showing compliance, and must receive updates and patches for the lifespan of the product, or at least 5 years after release (shortest of the two).
These measures, taken together, aim to ensure that products entering the EU market are resilient against current and emerging threats, and that they remain secure throughout their operational life.
Let’s now take a closer look at the most important obligations the CRA imposes on digital product providers, and see how PanIAM can help. PanIAM uses symbolic-reasoning AI to build a complete picture of your cloud infrastructure. We enable CISOs to focus on the most impactful vulnerabilities, quickly reducing both the potential likelihood of being targeted (attack surface) and the potential damage an attacker can cause (blast radius). PanIAM’s governance features help leaders keep cybersecurity risk under control, streamline communication with authorities on CRA compliance, and align with other regulations such as DORA or NIS2. Here are some specifics about how CRA compliance becomes easier with PanIAM:
| CRA Requirement | How PanIAM helps |
|---|---|
| Ensure secure default configurations (Art. 13, Annex I) | PanIAM facilitates the enforcement of least-privilege defaults and highlights overly permissive settings across cloud accounts so product defaults align with secure-by-default expectations |
| Minimize attack surface (Art. 13, Annex I) | PanIAM finds excessive permissions and exposed entry points, prioritizing reductions that most reduce attack paths’ blast radius |
| Protect against unauthorised access (Art. 13, Annex I) | PanIAM specializes in identity access management, helping organizations protect their assets against unauthorized access |
| Implement and maintain a cybersecurity risk management process (Art. 13, Annex I) | PanIAM provides continuous visibility on cybersecurity risks and change tracking that feeds risk assessments and supports documentation over time |
| Document and update cybersecurity risk assessment (Art. 13, Annex I) | PanIAM’s Timeline and audit features help evidence “best effort” and keep an up-to-date record of access-risk decisions |
| Provide software bill of materials (SBOM) (Art. 13, Annex I) | PanIAM’s solution tracks tools and packages used in code, ensuring up-to-date versions and security patches are used |
| Manage vulnerabilities efficiently (Art. 13, Annex I) | PanIAM helps prioritize fixes that most reduce risk, complementing your vulnerability-handling process |
| Report actively exploited vulnerabilities within 24 hours to ENISA (Art. 14-16) | PanIAM can help detect misconfigurations quickly, reducing time to discover issues |
While this table enumerates mostly technical obligations regarding products with digital elements, creating and documenting internal processes ensuring cybersecurity from design through implementation and into maintenance is also an important part of the CRA. It is reasonable to assume that, much like in the case of GDPR, being able to prove best effort of maintaining cybersecurity risk under control will be key to any CRA-based verification in the future. Reporting cybersecurity incidents within 24 hours will become mandatory in a year, with full implementation of the CRA in 2027. With PanIAM, meeting CRA obligations doesn’t mean adding more noise, it means cutting through it and focusing on what really matters. Start the process of protecting your business now by contacting PanIAM
We’ll continue to share updates as the CRA’s deadline gets closer. Consider subscribing to our newsletter to never miss essential cybersecurity news!
Stay Tuned
Subscribe to our newsletter and never miss our latest insights on cloud-native application protection and cybersecurity.
Subscribe Now