Introducing Secret Detection: A New Layer of Security in Your IAM & Network Graphs
By Jean-Yves PASQUIER on September 18, 2025

In modern cloud environments, identity and access management (IAM), network configurations, and encryption strategies are all critical pieces of the security puzzle. At PanIAM, we’ve built powerful capabilities to analyze these layers, helping you enforce least privilege, reduce lateral movement opportunities, and visualize your security posture through interactive graphs.
Today, we’re excited to announce a major addition: Secret Detection.
Why Secrets Matter
Secrets such as AWS access keys, Google Cloud credentials, GitHub tokens, or even social media API keys often become the weakest link in an otherwise well-protected environment. These credentials are commonly embedded in code repositories, configuration files, or logs—sometimes unintentionally. If leaked, they can grant attackers direct access to your systems, bypassing IAM controls and accelerating lateral movement inside your infrastructure.
Detecting and managing these secrets is not only about protecting isolated credentials. It’s about cutting off one of the most efficient attack vectors that adversaries use to escalate privileges and move across your environment.
What Our New Feature Brings
With Secret Detection, our platform extends its graph-based security analysis to cover exposed credentials. Here’s what this means for you:
- Automated Discovery: We scan your environment to identify common types of secrets, including cloud provider keys, API tokens, and OAuth credentials.
-
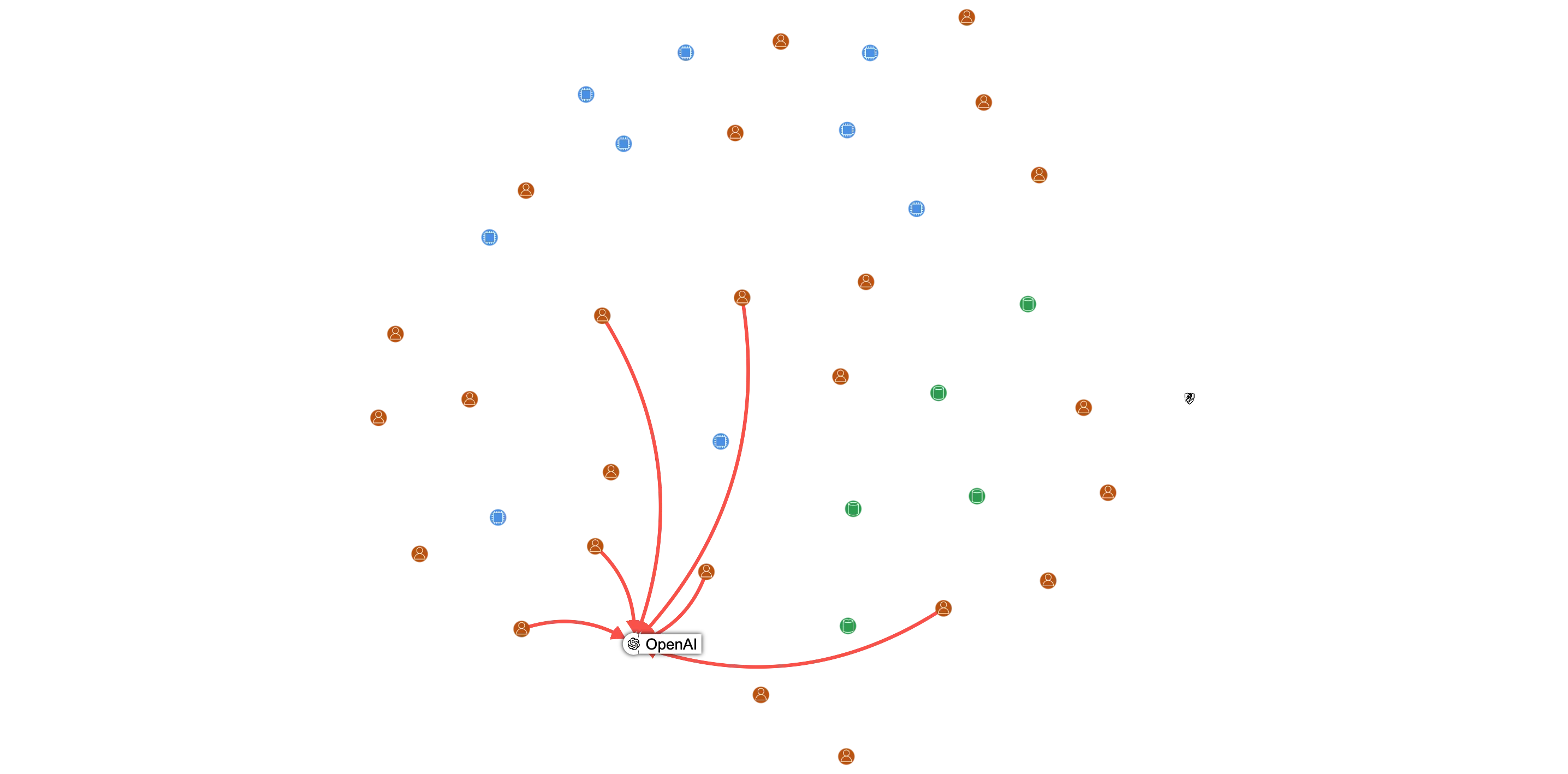
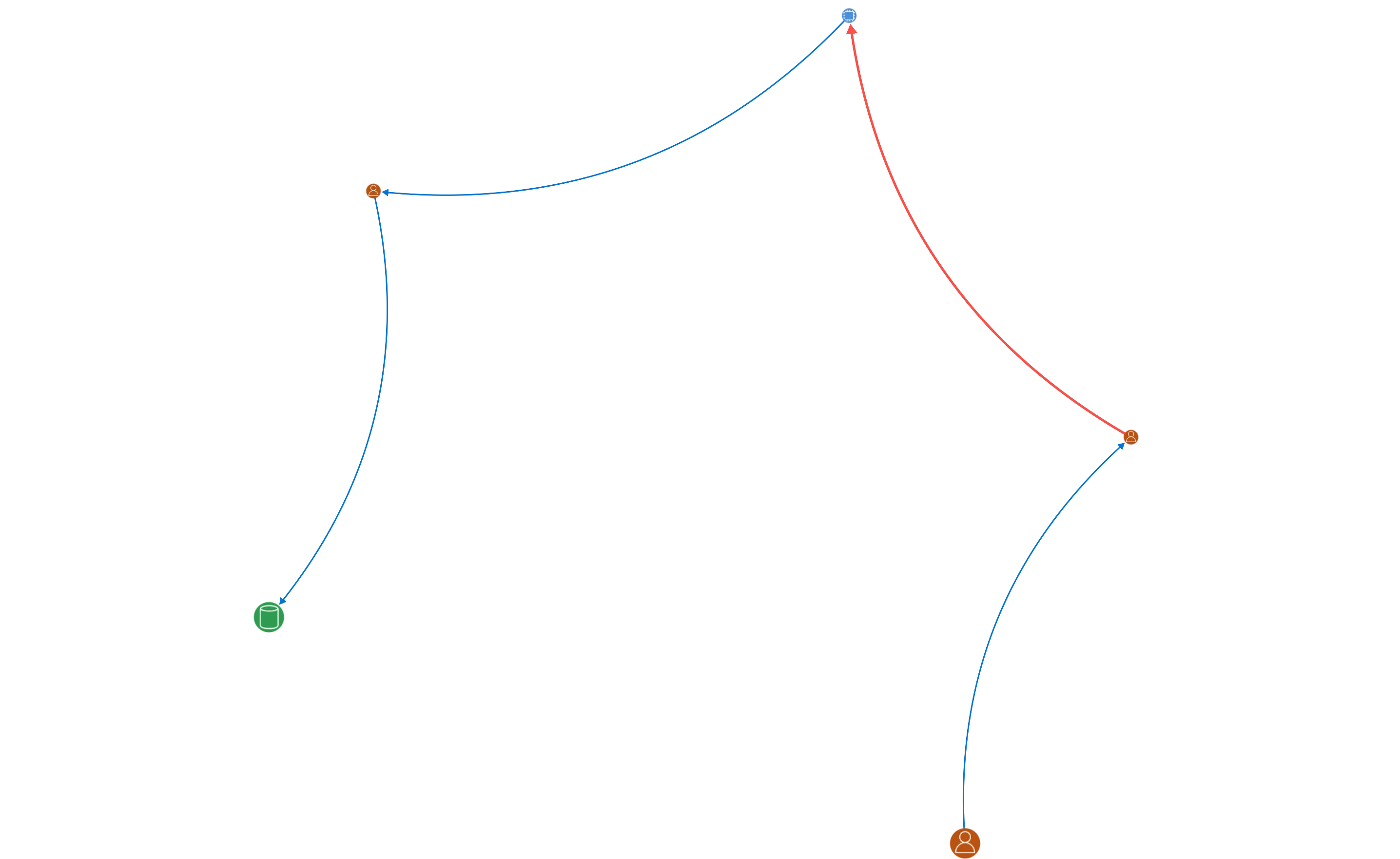
Contextual Graph Integration: Each discovered secret is placed in the security graph, showing how it connects to IAM identities and compute resources. This helps you see not just that a secret exists, but what it can actually access.
-
Lateral Movement Analysis: By linking secrets with IAM and network paths, our platform highlights how attackers could leverage them to pivot across your environment.
In addition to AWS internal access key, we handle these external secrets:
| OpenAI | GitHub | GitLab | Slack |
| Discord | Stripe | Twilio | SendGrid |
| Mailchimp | Telegram | Twitter/X | |
| npm | PyPI | Artifactory |
But of course, many more are coming soon !
Turning Visibility Into Action
The power of graph visualization is in making complexity simple. With secret detection integrated into your existing security graph, you’ll be able to:
- Instantly spot exposed credentials and understand their blast radius.
- Identify where least privilege policies break down due to hard-coded or leaked secrets.
- Prioritize remediation based on actual lateral movement risk, not just a list of potential leaks.
Instead of drowning in alerts, you gain an attacker’s perspective on your environment, but with the advantage of being able to stop them before they strike.
What’s Next
We are juste warming up. As we expand, we’ll continue to integrate more data sources, more advanced detection patterns, and deeper remediation workflows, all with the same graph-based visibility that sets our platform apart.
If you’re already using our platform, you can enable secret detection today from your dashboard. If not, get secure now and see how bringing IAM, network, encryption, and secrets together in one graph can give you the clarity and confidence your security team needs.
Stay Tuned
Subscribe to our newsletter and never miss our latest insights on cloud-native application protection and cybersecurity.
Subscribe Now