Introducing Remediations: Unified Risk Prioritization for Cloud Security
By Jean-Yves PASQUIER on November 24, 2025

Security leaders face a growing challenge: managing both IAM policy risks and software vulnerabilities across their cloud infrastructure. These two categories of risk typically live in separate tools, making it nearly impossible to answer a simple question: Which fix should my team work on first?
Today, we’re announcing a major expansion to PanIAM: Remediations. This feature brings software vulnerability analysis into the same unified dashboard as IAM policy risks, with quantified risk metrics that help you prioritize based on real-world impact.
The Challenge: Scattered Priorities
Most organizations juggle multiple security tools. Vulnerability scanners produce lists of CVEs sorted by severity. IAM analysis tools flag policy misconfigurations. Each tool has its own scoring system, its own dashboard, and its own definition of “critical.”
The result? Security teams struggle to compare apples to oranges. Is a “critical” CVSS vulnerability more urgent than a “high” privilege escalation risk? Without a unified view, prioritization becomes guesswork.
Even worse, traditional severity scores don’t reflect real-world risk. A vulnerability with a high CVSS score might never be exploited in the wild, while a “medium” vulnerability could be actively targeted by attackers.
Our Approach: Risk-Based Unification
PanIAM now analyzes your internet-connected compute resources (EC2 instances, ECS services, AWS Lambda) for package vulnerabilities, your IAM policies for misconfigurations and generates actionable remediations. But we don’t just count vulnerabilities — we calculate the probability that your resources will be compromised based on real-world exploit data.
This means every remediation, whether it’s a policy fix or a package update, comes with a quantified risk reduction score. You can finally compare different types of fixes on the same scale and prioritize by actual impact.
What Security Leaders Get
Unified Risk Dashboard
See all your security remediations in one place. Policy fixes and package updates appear side by side, each with clear risk metrics. No more switching between tools to understand your security posture.
Real-World Risk Prioritization
We analyze which vulnerabilities are actually being exploited in the wild, not just their theoretical severity. This filters out the noise and surfaces the fixes that will genuinely reduce your attack surface.
Clear Time-to-Remediation Estimates
Not all fixes are created equal. Our system categorizes remediations by effort required:
- Quick: Fixes that requires minor modifications that can often be automated, like fixing undue AWS access keys
- Medium: Fixes that may require some changes in the architecture or some manual review, eg moving a secret inside a secure vault
- Long: Policy or architectural changes that need careful planning, like updating to a new major version of a package or service
This helps you balance immediate wins against larger initiatives.
Focus on What Matters
We only analyze compute resources that are reachable from the internet. These are the systems attackers can actually target. This focus ensures you’re not wasting cycles on vulnerabilities that can’t be exploited remotely.
Remediations handled
Package updates are categorized as minor (patch/minor version) or major (new major version):
- Minor updates carry low risk of breaking changes and can often be applied in bulk
- Major updates may require code changes and careful testing
This distinction helps you plan your remediation workflow—quick wins with minor updates, then scheduled work for major ones.
But we also handle Policy-based Remediations that prevent privileges escalation or lateral movement
Measuring Security ROI
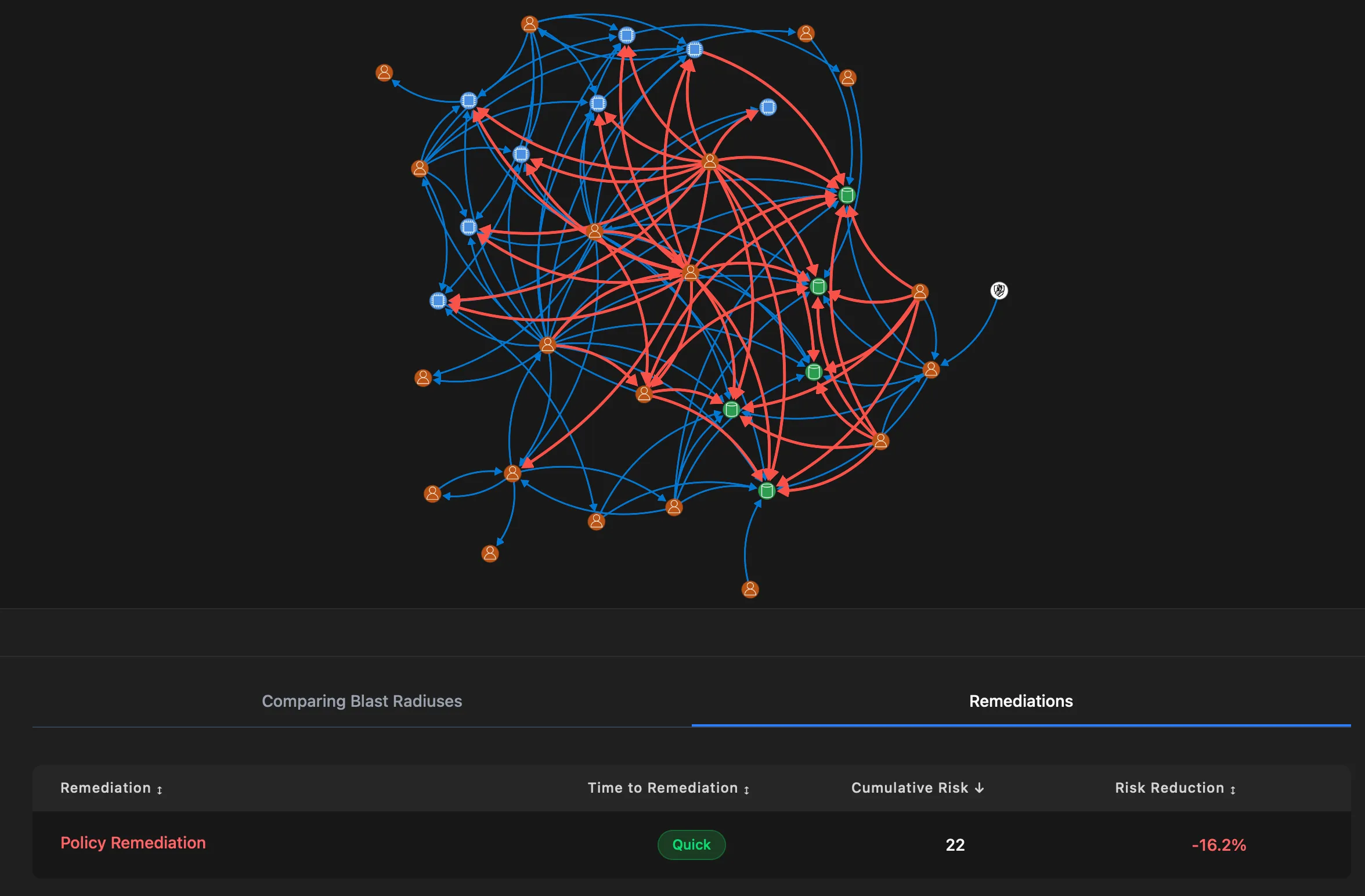
Each remediation in PanIAM shows two key metrics:
- Cumulative Risk Score: Your current risk level for the affected resources
- Risk Reduction Percentage: How much this fix will reduce your overall risk
These numbers transform security from a qualitative exercise into a data-driven discipline. You can show stakeholders exactly how much safer each fix makes your environment, justifying security investment with concrete metrics.
Built on Deep Research
This feature represents months of R&D work from our team. We’ve built systems that analyze exploit patterns across the threat landscape, calculate compound risk across multiple vulnerabilities, and map how those risks connect to your specific AWS resources.
The result is a remediation engine that doesn’t just find problems—it tells you which ones to fix first and quantifies the value of each fix.
Available Now
Remediations are live in your PanIAM dashboard today. If you’re already using PanIAM for IAM analysis, you’ll now see package remediations alongside your policy fixes, complete with risk metrics and prioritization guidance.
Not yet using PanIAM? Contact our team for a demo and see how unified, risk-based remediation prioritization can transform your security operations.
What’s Next
We’re continuing to expand PanIAM’s coverage, bringing the same risk-based approach to new areas of cloud security. Our goal is to give security leaders a single source of truth for all security priorities, with the quantified metrics needed to make confident decisions.
The days of guessing which vulnerabilities matter most are over. Welcome to risk-based security prioritization.
Stay Tuned
Subscribe to our newsletter and never miss our latest insights on cloud-native application protection and cybersecurity.
Subscribe Now